WannaCry Ransomware Campaign
A massive ransomware campaign, called ‘WannaCry’, appears to have infected a number of organisations around the world. Computers in thousands of locations, in more than 150 countries have been locked by a program that demands the equivalent of about $300 in Bitcoin to be unlocked.
The main difference between WannaCry and other ransomware is the ability to spread itself within corporate networks, without user interaction.
At least three Australian companies have been hit, possibly more, says the Government. Europol spokesman fears attack not over as “numbers are going up”.
Microsoft have released a new patch to further protect against this threat, it has been installing on Servers and Desktops during this weekend.
Royal IT is closely monitoring the deployment of the patch for all Managed Services Customers.
Customers using Webroot antivirus are protected and Windows 10 is not affected by the virus.
The threat has apparently stopped circulating the Internet but sources are warning a new version of the threat (different code) may be released soon.
Email is one of the main infection methods. Be wary of unexpected emails especially if they contain links and/or attachments.
Be extremely wary of any Microsoft Office email attachment that advises you to enable macros to view its content. Unless you are absolutely sure that this is a genuine email from a trusted source, do not enable macros and instead immediately delete the email.
The security of your assets is a layered approach, no one preventative measure will keep you 100% safe from threats, but by combining multiple strategies – you can minimise your risk to exposure and safeguard your assets going forward.
You can find more information about the outbreak on Wikipedia
What to watch for in emails
As spam is a normal, albeit potentially dangerous part of normal day to day IT – here are some tips to determine if an email you received is spam or not:
Check the senders email address by double clicking the contact on a received email within Outlook and verifying both email addresses. Note that just because the email addresses are the same, the email may still be spam;
Be very wary of emails coming from: The ATO, Australia Post, ANZ and ANY emails saying you have received money and you cannot verify the sender. Delete the email immediately if you receive emails from any of the mentioned senders with any attachment/s.
If you are unsure of the sender and the email contains attachments types: DOC, DOCX, ZIP, EXE. Delete the email immediately, do not open the attachment as these types of files can execute code to damage your machine and other machines on the network. We have seen a number of spam emails that advise of payment with a receipt or invoice attached. The attachment is of the DOC or DOCX type. This is the first sign that the email is potentially spam. Most companies will send receipts and invoices as PDF’s.
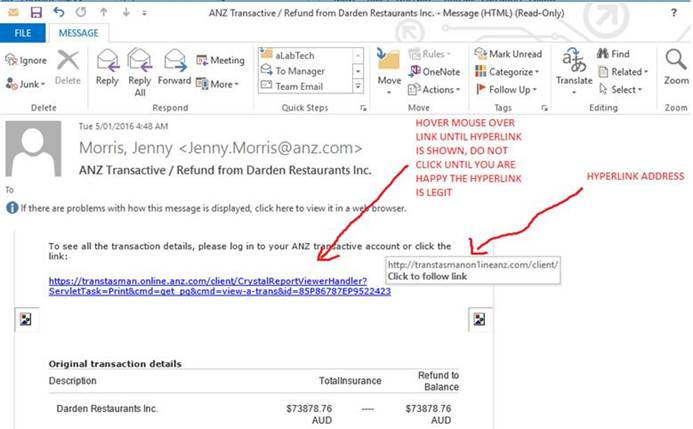
If you receive an email with a link and you are unsure of the sender, delete it! If you feel the need to check, hover your mouse over the link until the true hyperlink is shown. If this hyperlink is unknown or differs, do not click the link. In the below example, the email is spam and the hyperlink is changed only slightly to the original link text. The actual website and location are completely different to the original text, in IT talk this is called ‘phishing’;
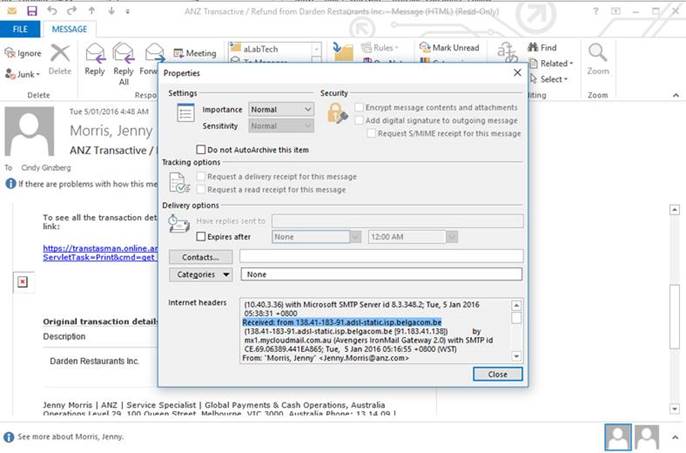
ADVANCED USERS; check the headers of a received email to check and verify the DNS address/IP address of the sender. You can generally tell a spam email by the domain name of the incoming mail server or checking the IP address geolocation on www.iplocation.net
Anti-Virus Protection
All machines should be protected my an anti-virus application. The anti-virus application alerts on any infections found and if the anti-virus is unable to update its virus/malware definitions.
All anti-virus or anti-malware programs will not detect all threats but they are essential tools in defending against all types of malicious code. If your anti-virus appears on your screen with ‘threats detected’ or the like, please shutdown your computer immediately to remove the risk of further damage and advise your IT department immediately.

